How to protect yourself from Packet Sniffers
When you do anything online, you’re sending packets of data all across the globe. To simplify, think of it this way: when you type in a web address in your browser or post a new update on your social media channels, your information gets broken down into packets of data and sent to its intended destination.
Whether it’s a computer, a smartphone, a tablet or any other device, information is broken down into tiny packets and sent to data centers thousands of miles away. If you think that you and the receiving end are the only ones who have clear access to these data packets, you might want to reconsider.
Experts would argue that you are not the only parties that might have access to the data. While you may believe you’re the only one, somewhere someone would be sitting and sniffing on any and all information that travels through the wires of your local network and the internet.
What is a Packet Sniffer?
A packet sniffer is a software or an individual who closely monitors and analyzes your network traffic to discover glitches and improve the efficiency of the network. A packet sniffer isn’t necessarily evil-minded, and it could be the IT guy at your office.
The sniffer attack may use its power to infiltrate your network and clearly observe the ins and outs of your online activities.
A packet sniffer can monitor nearly everything that passes through them, including unencrypted passwords and usernames which can then be used by hackers who continuously target sniffers to gain uninterrupted access to a wide range of information.
There are two main types of packet sniffers:
- Hardware Packet Sniffers
A hardware packet sniffer is designed to be plugged into a network and to examine it. A hardware packet sniffer is particularly useful when attempting to see the traffic of a specific network segment. By plugging directly into the physical network at the appropriate location, a hardware packet sniffer can ensure that no packets are lost due to filtering, routing, or other deliberate or inadvertent causes. A hardware packet sniffer either stores the collected packets or forwards them on to a collector that logs the data collected by the hardware packet sniffer for further analysis. - Software Packet Sniffers
Most packet sniffers these days are of the software variety. While any network interface attached to a network can receive every bit of network traffic that flows by, most are configured not to do so. A software packet sniffer changes this configuration so that the network interface passes all network traffic up the stack. This configuration is known as a promiscuous mode for most network adapters. Once in promiscuous mode, the functionality of a packet sniffer becomes a matter of separating, reassembling, and logging all software packets that pass the interface, regardless of their destination addresses. Software packet sniffers collect all the traffic that flows through the physical network interface. That traffic is then logged and used according to the packet sniffing requirements of the software.
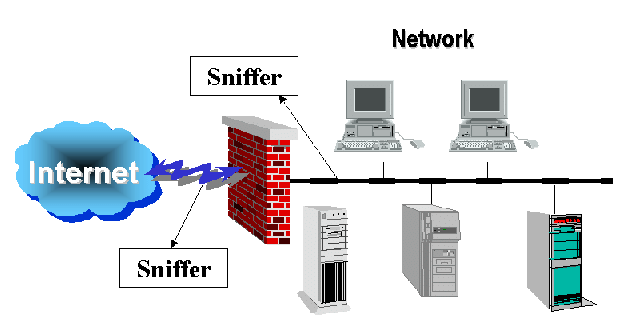
Capturing data on an entire network may take multiple packet sniffers. Because each collector can only collect the network traffic that is received by the network adapter, it may not be able to see traffic that exists on the other side of routers or switches. On wireless networks, most adapters are capable of connecting to only one channel at a time. In order to capture data on multiple network segments or multiple wireless channels, a packet sniffer is needed on each segment of the network. Most network monitoring solutions provide packet sniffing as one of the functions of their monitoring agents.
Common Network Analyzers :
The following list contains some common analyzers:
- Wireshark
- Ettercap®
- Dsniff®
- Tcpdump
- Etherpeak®
- Cain and Abel®
How to defend against sniffing
Use the following techniques and best practices to protect yourself from sniffing attacks:
- Restrict the physical access to the network media to ensure that a packet sniffer cannot be installed.
- Use encryption to protect confidential information.
- Permanently add the MAC address of the gateway to the ARP cache.
- Use static IP addresses and static ARP tables to prevent attackers from adding spoofed ARP entries for their machines to the network.
- Turn off network identification broadcasts, and if possible, restrict the network to authorized users in order to protect the network from being discovered with sniffing tools.
- Use the IPv6 instead of the IPv4 protocol.
- Use encrypted sessions such as Secure Shell (ssh) instead of Telnet.
- Use Secure Copy (scp) instead of a file transfer protocol (ftp).
Use Secure Socket Layer (SSL) for email connections.
Apart from encryption, a Wi-Fi VPN is armed with security protocols that ensure that your encoded data passes through guarded tunnels and reaches its destination untouched. With AES 256-bit encryption, you can rest assured about your online privacy and security.
Additionally, you should check the website’s security by ensuring that you only visit encrypted websites (starting with https). HTTPS refers to Hypertext Transfer Protocol Secure, and as opposed to HTTP, the S at the end can go a long way in securing and preventing packet sniffers from seeing the content or the specific page you’re visiting.
If you want to remain secure on the web and keep away from packet sniffers, you have to stay on top of the game. You can’t rely on other tools all the time as the best security comes from you. If you’re not taking security as a primary concern, then you really can’t expect tools to keep you masked at all times.
Like any other security tool, packet sniffers have loads of good and evil usages. It eventually depends on the intention of the user; nonetheless, you must use precautionary measures to stay secure.

